Exposed Quadream spyware control web panel
Or how an exposed source code repository lifts it's veil on this mysterious company
(Please also read the story on Haaretz)
Little is known about Quadream, an Israeli spyware manufacturer. Reuters wrote that they possess a zero-click mechanism to infect iPhones through iMessage. Customers are allegedly Saudi Arabia, Mexico, Singapore and Indonesia.
Quadream had an office in Ramat-Gan, Israel as well as a subsidiary, ‘InReach Technologies’ in Cyprus. The two entities had a falling out and a settlement was announced by their barrister acting in the case worth $6 million.
This all started out in a Cypriot court about the non-payment of invoices in 2020.
My information indicates that prior to this announcement all staff were laid off in the Cypriot company around July/August of 2020. A source provided me with information that suggests that a server temperature alert was never acknowledged after August of 2020. Which seems to suggest that indeed everyone was laid off around that time.
In mid 2020 I was approached by a source who mentioned they had found an repository on Github. The repository in question was the source code of the web panel of their REIGN spyware agent. The source code repository had a last commit on the 23th of May, 2019.
I’ve been able to verify this is legitimate as one of the developers who appeared in the git repository posted on LinkedIN that the company was hiring in Ramat-Gan where Quadream was located posted the following on LinkedIn.
Email-addresses that were used in the git commits were all ‘quadream.io‘. This was obtained from one of the developers who posted on Linkedin. I also managed to confirm it with a different source who used to work for Quadream.
The Israeli developers who worked on the web panel were laid off as that work was moved to InReach Technologies in Cyprus in the second quarter of 2019.
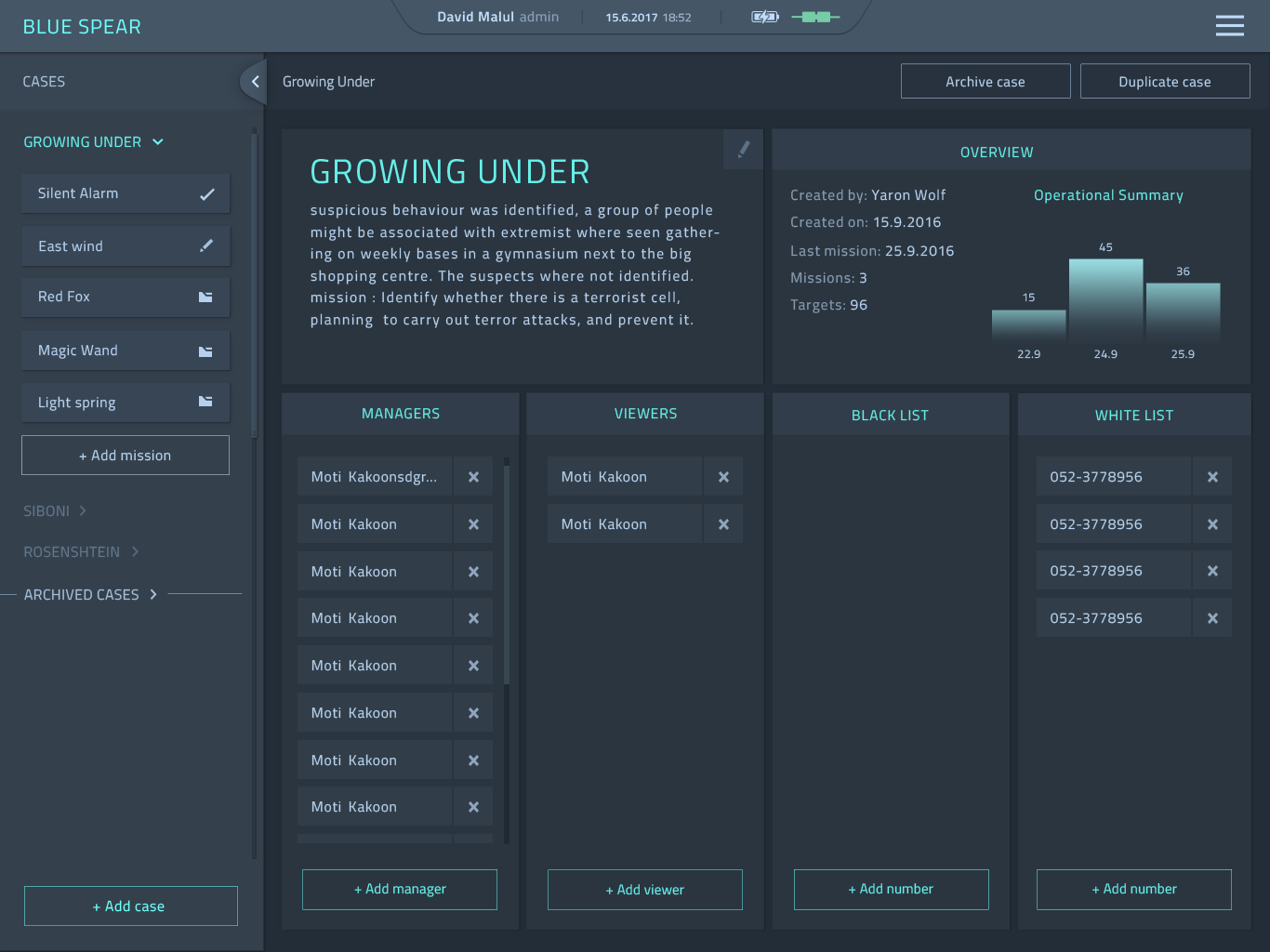
The above image was found in the git source code repository. I’ve tried to compile from the latest commit but it lacks an internal package that wasn’t included in the repository. However, an earlier commit that I did manage to build at least has the same color scheme and menu layout as that version included an earlier missing internal package that was once committed.
As we can see on the left menu bar are different cases, a case can have multiple missions, e.g, multiple infected phones.
In the central menu there’s also a mention of: ‘GROWING UNDER‘ the active case in question. Lists a manager, viewers, a black list and a whitelist of phone numbers that can be targeted.
The git repository has multiple names for the web panel, BLUE SPEAR and QuantumUI. Presumably, QuantumUI is the actual name as that’s also appears in the React package.json.
Guy Geva, one of the Quadream founders, seemed semi-active in the development of the web panel as he has several commits in the git repository.
Capabilities
It seems that in 2019 there was only support for iOS infection, not for Android. While there are some Android references, but only with a mention of “Android 6s” in a file named “mission-failed.json”
While no spyware agent code is included in the repository, there’s some indicators of what the agent is supposedly capable of.
It’s said to be able to extract information from:
Signal
Telegram
Whatsapp
Viber
Skype
Twitter
Wickr
Messages
FB Messenger
Line
Hangouts
Mail
Call(s) (history)
Contacts stored in the phone
Location
Wechat
Photos
List of applications
Keychain extraction like passwords.
Vector types
There’s three alleged infection vectors which can be used to infect a phone.
Pioneer
X-Caliber
WhatsApp (shows up later)
src/app/models/devices.ts
17: vectorType: string; //pioneer, x-caliber ...Mostly X-Caliber shows up in the data generated in json files. Pioneer is listed as a vector but from both it’s not entirely clear what exactly what software is targeted here.
We can however more broadly learn more about the vectors used to target phones.
cat src/assets/jsons/target/defaults.json | grep vector | sort -u
"vector": "link",
"vector": "whatsapp",
"vector": "x-caliber",This file was first committed on the 27th of December 2018 and it didn’t change content. (A good reminder that NSO was caught in May of 2019 of abusing an WhatApp exploit and subsequently got sued by WhatsApp.)
From another json file we can learn some more.
cat src/assets/jsons/mission/active-mission-int.json | grep vector | sort -u
"vector": "banner",
"vector": "interceptor",
"vector": "link",
"vector": "x-caliber",So now we have a list of what’s possible and we can learn more about what kind of zero-days they’ve had in the past.
Looking at other files we learn that it has a built-in check to valid both phone numbers and email-addresses. It will first validate a phone and else it will check whether the email-address you put in is valid.
if (input.length > 0) {
if (this.selectedType === 'phone') {
const phoneRegex = new RegExp(
/\+(9[976]\d|8[987530]\d|6[987]\d|5[90]\d|42\d|3[875]\d|2[98654321]\d|9[8543210]|8[6421]|6[6543210]|5[87654321]|4[987654310]|3[9643210]|2[70]|7|1)\d{9,14}$/
);
if (!phoneRegex.test(input)) {
this.error = 'Invalid phone number';
} else {
this.error = null;
this.vector.identifier = input;
}
} else {
const emailRegex = new RegExp(
/^(([^<>()\[\]\\.,;:\s@"]+(\.[^<>()\[\]\\.,;:\s@"]+)*)|(".+"))@((\[[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}])|(([a-zA-Z\-0-9]+\.)+[a-zA-Z]{2,}))$/
);
if (!emailRegex.test(input)) {
this.error = 'Invalid email address';
} else {
this.error = null;
this.vector.identifier = input;
}
}X-Caliber comes with a set of licenses and will also maintain what has been used so far. Although that hasn’t been handled dynamically yet when reviewing the latest commit.
this.vector = {
name: 'X-Caliber',
license: {
used: 10,
total: 100,
tip: 'Tip'
},
vectorStateTip: '',
vectorState: '',
vectorType: 'x-caliber',Last but not least, one file lists which of these need licenses.
[
{
"id": "12423fdr2342d32",
"vector": "x-caliber",
"name": "Silver Bullet",
"enabled": true,
"reason": {
"text": "Resource not available",
"severity": "warn"
},
"tooltip": "Use it wisely",
"vectorState": "NO_LICENSE",
"maxActions": 0,
"inputs": {},
"licenses": [
{
"used": 0,
"total": 250
}
],
"checked": false
},
{
"id": "24213rfedg45634r22r43534t",
"vector": "link",
"name": "Link",
"enabled": true,
"vectorState": "OK",
"maxActions": 1,
"reason": {
"severity": "warn"
},
"tooltip": "Use it wisely",
"inputs": {},
"licenses": [
{ "used": 1, "total": 10 }
],
"checked": false
},
{
"id": "eq12e3e3r42r32e3r34r",
"vector": "whatsapp",
"vectorState": "INIT",
"maxActions": 2,
"name": "WhatsApp",
"enabled": true,
"reason": {
"severity": "warn"
},
"tooltip": "",
"inputs": {},
"licenses": [],
"checked": false
}
]However, it’s unclear what “x-caliber” or “pioneer“ exactly targets on iOS.
I can also confirm that the name of the spyware agent is indeed REIGN.
src/app/services/svg-json-icons/svg-icons.service.ts
305: case 'transferring-to-reign':
306: return `<svg viewBox="0 0 12.86 18.86" id="transferring-to-reign" width="${size ? size : ''}" height="${size ? size : ''}">
1180: case 'move-to-reign-device':
1181: return `<svg viewBox="0 0 15 15" id="move-to-reign-device" width="${size ? size : ''}" height="${size ? size : ''}">
1198: case 'reign-completed':
1199: return `<svg viewBox="0 0 11.37 17.46" id="reign-completed" width="${size ? size : ''}" height="${size ? size : ''}">Interacting with the agent
if an agent is already on the phone, it won’t infect the phone again. Which might be interesting if two Quadream customer ever find themselves targeted the same phone.
"value": "Agent already exist in the source",The agent can also be (forcefully) terminated.
terminateAgent: '/sources/{{id}}/shutdown',
forceTerminateAgent: '/sources/{{id}}/force_shutdown',Pioneer shows up again.
// Pioneer Devices
queryPioneerDevices: '/pioneers/query/by_target/{{id}}',
resetPioneerMachine: '/pioneers/{{id}}/reset',
checkPioneerDevice: '/pioneers/check/{{target_id}}/{{device_id}}',
attackPioneerDevice: '/pioneers/infect/{{target_id}}/{{device_id}}',
abortPioneerDevice: '/pioneers/abort/{{target_id}}/{{device_id}}',We can also learn more about the tasks that were implemented at the time.
// Tasks
// getSourceDeviceInfo: '/sources/{{id}}/deviceinfo',
// getSourceChat: '/sources/{{id}}/{{chatType}}',
getSourceIntels: '/sources/{{id}}/apps',
getTasks: '/sources/{{id}}/tasks',
getSourceIntel: '/intls/sources/{{id}}/{{intelName}}',
taskAction: '/sources/{{id}}/cnc/{{taskAction}}',
getSessionMessages: '/intls/sources/{{source_id}}/{{chat_name}}/sessions/{{session_id}}',
getSessions: '/intls/sources/{{source_id}}/{{chat_name}}/sessions',
getMedia: '/media/{{media_id}}'
// /intls/sources/{id}/whatsapp/sessions
// intl/sources/<sourceId>/deviceinfoOr for more generic tasks.
// Messengers
getChatAppChats: '/messengers/{{type}}/sessions',
getChatAppInfo: '/messengers/{{type}}/about',
// Applog
getEvents: '/events',
getRightBar: '/dashboard/right',
dismissEvent: '/events/{{id}}',
// Targets
targets: '/targets',
archiveTarget: '/targets/{{id}}/archive',
findDevices: '/targets/{{id}}/devices',Scanning the internet
Unfortunately, I’ve not been able to find any historical deployments on both Shodan and Censys. It might be possible that the web panel was protected by a firewall. An indicator is: <title>QuantumUi</title>
If you have any possible hits in any of your historical data, please let me know!
Job advertisement
Quadream employees can be hard to find on LinkedIN. They don’t advertise for positions and don’t have a website. This is on purpose I found out. However, one of the developers for the web panel once posted they were hiring, but they hire under the moniker of: 4dco.
The decoders position that I archived confirms some of the findings that Microsoft threat intelligence just published about. That Go as a programming language was used for their agent.
There’s also evidence of Go in the Makefile of the repository
ifndef QD_GO_ROOT
$(error 'QD_GO_ROOT not exists')
endif
QD_GO_MAKEFILE_PATH := ${QD_GO_ROOT}/sr-rnd-00.swg.local/go/makefile
include ${QD_GO_MAKEFILE_PATH}/Makefile.base
RELEASE ?= 1
NG_BUILD_ARGS ?=
ifeq (${RELEASE},1)
NG_BUILD_ARGS += --prod
endifThe decoders group basically work to make the spyware REIGN agent leave as little traces as possible on both Android and iOS. Do potential data recovery on the phone, exfiltrate and work on decryption of encrypted data on the smartphone.
Another position that InReach technologies advertised that they were hiring for researchers that would be looking for vulnerabilities in both Android and iOS.
Hope you enjoyed this little write-up. I don’t intend to link to the source code repository.
Want to share more?
Do you have knowledge of these services or want to share gossip about your competitors? This gist on github explains how to contact me securely.